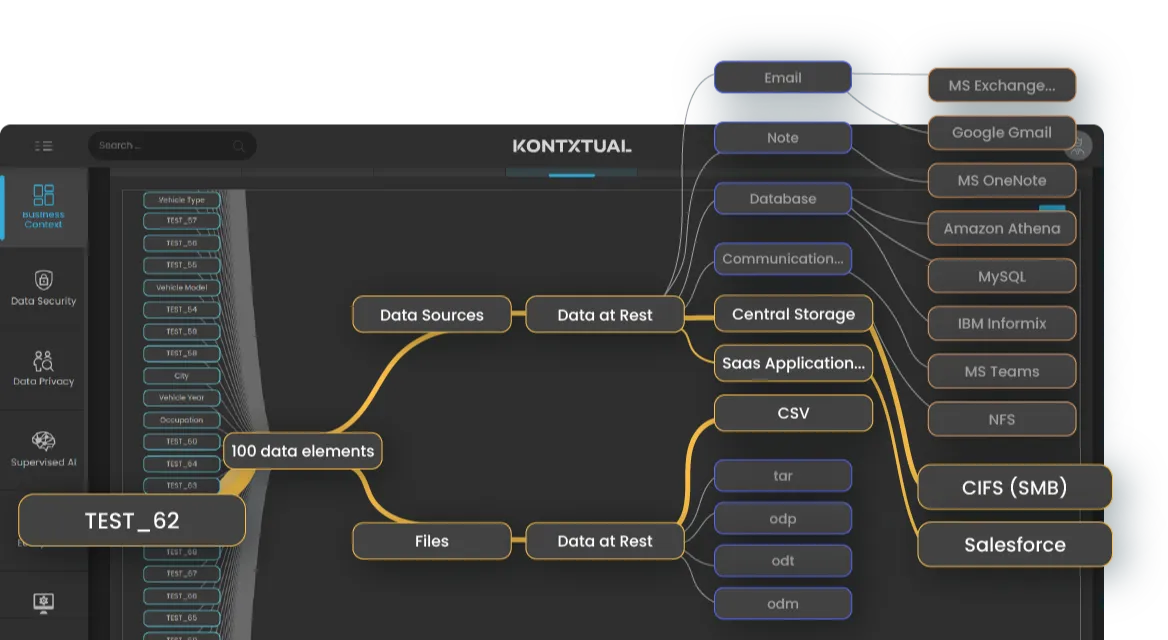
Make Access Risk Visible—and Actionable
Know exactly who has access to sensitive data, where, and why. KontxtualTM Access Intelligence by 1touch.io replaces static permission lists with continuous, contextual visibility across your hybrid environment. Uncover risky access paths, surface the business context, and take real-time action to close gaps before they become incidents.