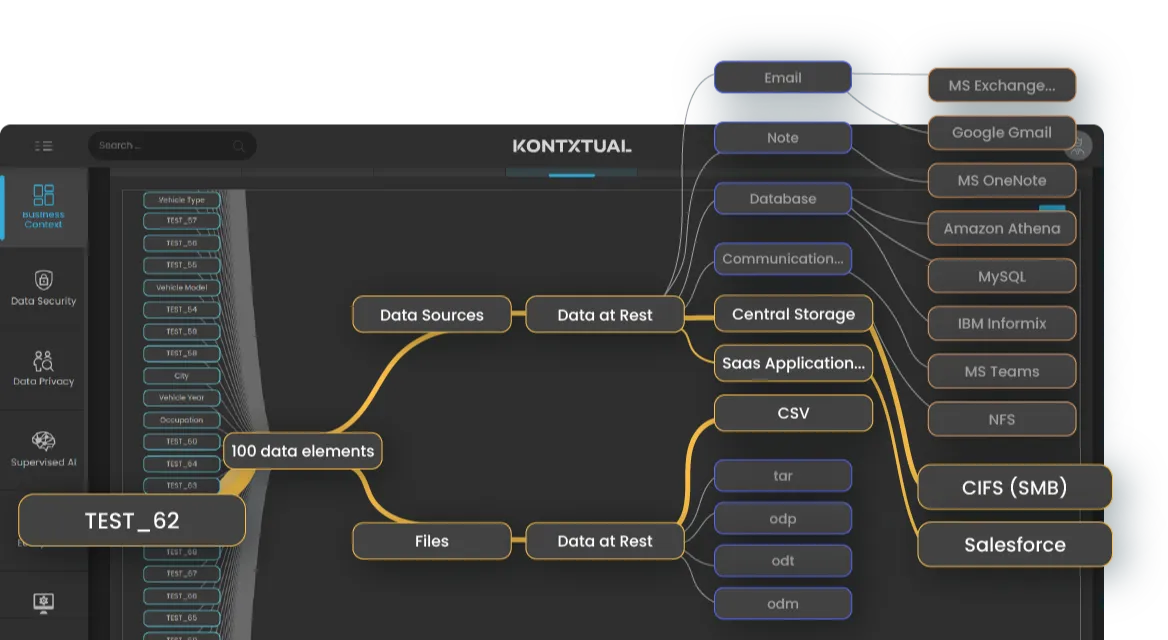
Quantum disruption may be on the horizon, but cryptographic risk is already in your environment. Most organizations don’t know where all their keys, tokens, or certificates live or which ones are expired, misconfigured, or dangerously exposed. Those unmanaged non-human identities leaves posture weak, audits in jeopardy, and governance incomplete.
KontxtualTM fixes this with continuous, real-time visibility into every cryptographic assets and non-human identities across SaaS, cloud, mainframe, and on-prem storage systems. Each secret is classified in context, mapped to risk, and tied to the next best action, so teams can focus on resolution, not manual triage.