October 25, 2022
IBM and 1touch.io announce a breakthrough solution to increase value for GDP customers with IBM Secu
Marketing
October 25, 2022
Marketing

1touch.io in partnership with IBM Security, are pleased to announce the upcoming release details for IBM Security Discover and Classify (ISDC) version 3.0 powered by 1touch.io’s Inventa which is the market’s first dedicated discovery and classification solution for important sensitive data. ISDC is a major step in the joint vision to create the world’s greatest discovery and classification tool with precise sensitive data intelligence that feeds existing security investments to minimize business impact and enhance overall security and privacy.
Key features for V3.0
One key feature to elaborate on is the integration with Guardium Data Protection. Today, GDP can do classification for structured data using Regex and keywords, which are two main methods of classification in any product. ISDC compliments that approach by also using Functions and Dictionaries in conjunction with AI/ML approaches to classify not only at the schema or table but down into the field/record and actual data element. Similarly, ISDC provides classification for unstructured and semi-structured data.
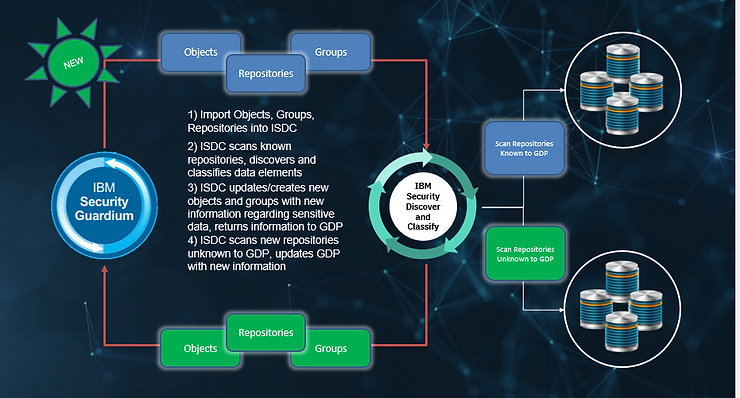
Similarly, there is a workflow integration to automate the creation of Groups and Objects into GDP. The slide below shows the workflow where 1) GDP sends to ISDC a list of Objects, Groups and Repositories that are known 2) ISDC scans the known repositories and classifies at the data element level using the capabilities mentioned above 3) ISDC updates and/or creates new groups in GDP with new information regarding sensitive data 4) ISDC then scans repositories unknown to GDP so GDP can protect them. This integration provides the best of both tools: ISDC to discover and classify sensitive data and GDP to protect and monitor sensitive data.
To learn more, 1touch.io and IBM Security are hosting a webinar on 10/25 which will be recorded for future consumption. Please reach out to us to get a demo!
%202.png)
From Data Maps to Data Navigation: Why Enterprise AI Needs Context to Stay Trustworthy
All Industries
February 6, 2026

Why Enterprise AI Agents Fail Without Context: The Pitt’s Lesson for Data Security
All Industries
February 3, 2026

Why Traditional DSPM Solutions Fall Short in an AI-Driven World
Data Security
All Industries
January 30, 2026